Recently, I found a security issue with the way IT-Boost handles TOTP secrets.
IT-Boost can calculate OTP codes, making it ideal for sharing credentials within a team. When a user loses access to IT-Boost, they also lose access to the credentials and TOTP generator. However, it turns out that TOTP secrets may not be as secure as assumed since the codes are calculated in the browser instead of on a backend server.
Blog by Jeremy Pot.
TOTP Secret exposure risks
- Extraction of TOTP Secrets: Users can extract TOTP Secrets and install a new TOTP generator on another device. This vulnerability is particularly concerning when an employee leaves the company, potentially retaining access to sensitive accounts.
- Compromised Devices: Malware and Remote Access Trojan (RAT) kits can be used by threat actors to record usernames, passwords, and TOTP Secrets. This can lead to a massive security breach, affecting numerous services and customers.
Best Practices for TOTP Code Generation
The correct way of providing TOTP codes to a user, would be to leverage a TOTP API endpoint, where the TOTP code is calculated. This method ensures the TOTP Secret isn’t transferred to the browser.
Response and Recommendations
We reported our findings to the ConnectWise compliance team, who confirmed the issue on 24 June 2024. They will be releasing a fix for this issue tomorrow, on 25 Juli. We recommend all IT-Boost users to cycle their TOTP Secrets as soon as the security update is implemented. This will help mitigate the risk of compromised OTP Secrets.
Screenshots Demonstrating the TOTP Secret Vulnerability
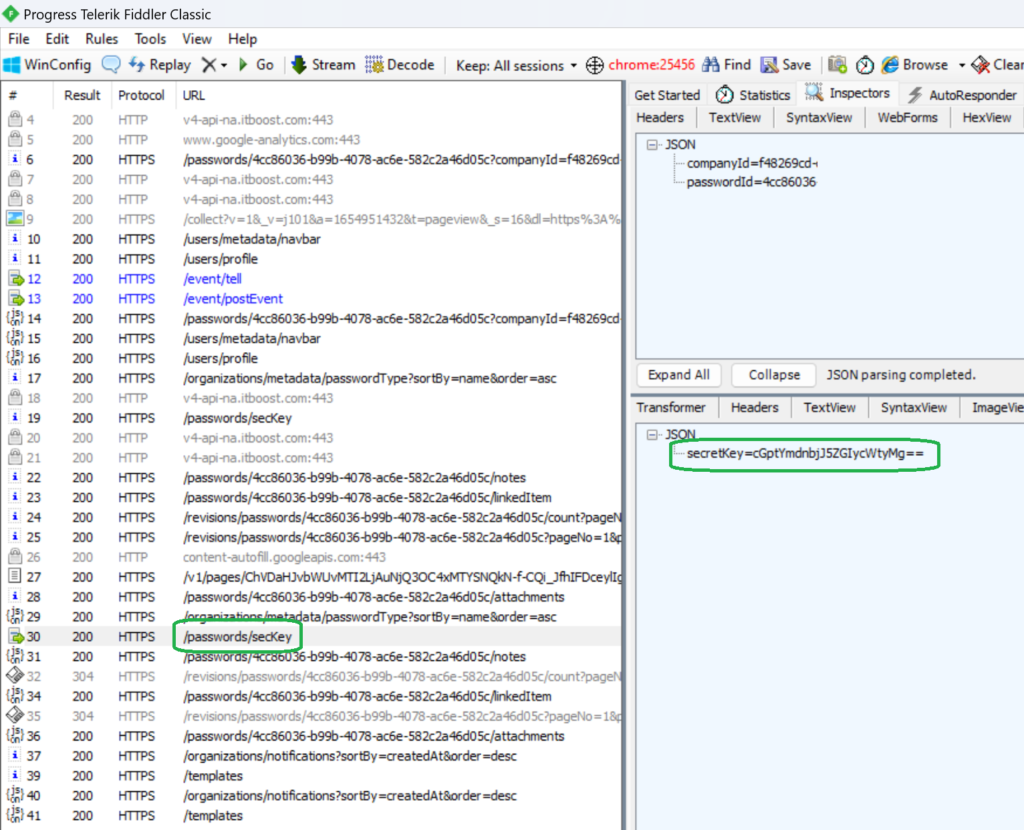
Below is a Fiddler request for opening a password stored in IT-Boost. The secretKey value is a base64 string which, when decoded, is the same as the TOTP Secret we provided when submitting credentials.
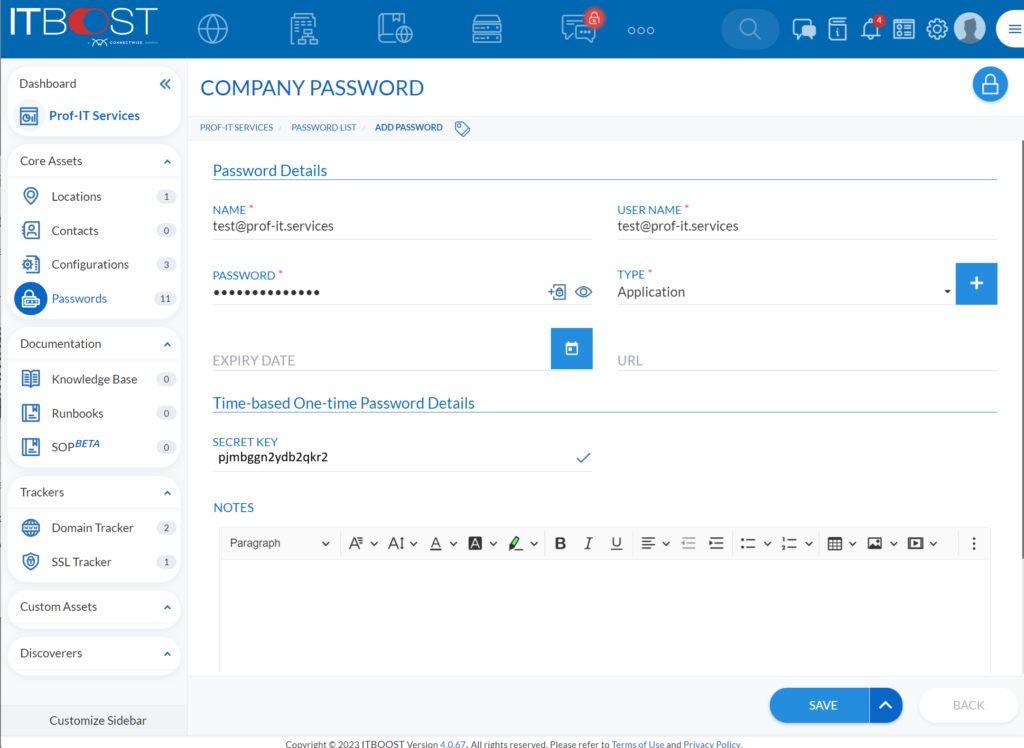
New password entry, with secret: pjmbggn2ydb2qkr2
The /passwords/secKey endpoint returns a JSON value with a base64 encoded string, which is the same as the provided secret: cGptYmdnbjJ5ZGIycWtyMg== decoded value: pjmbggn2ydb2qkr2
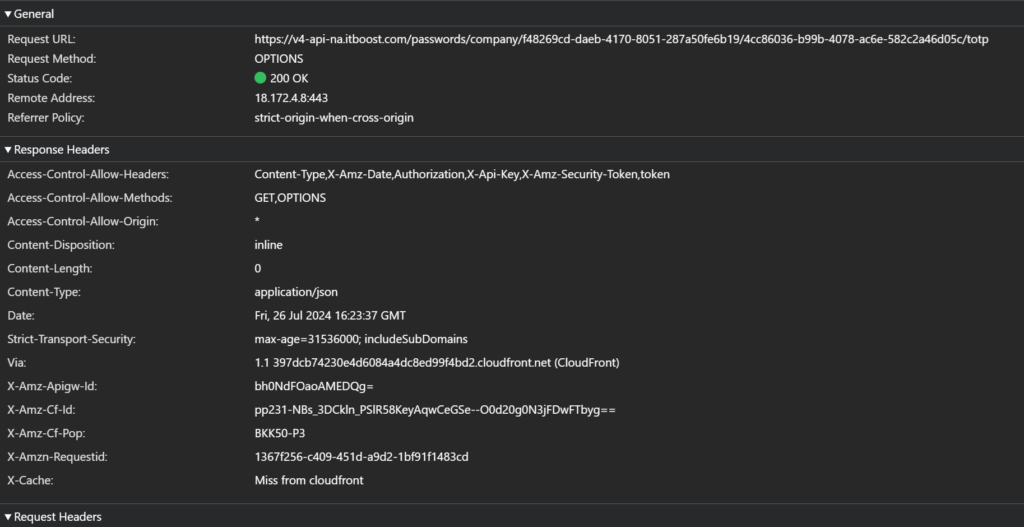
Update 2024-07-26
The vulnerability is now resolved as an TOTP api endpoint is used.


No responses yet