Please read blog 2, using Log Analytics is more cost effective and doesn’t have a 10 entity limit.
https://potsolutions.nl/2023/05/20/block-sentinel-log-analytics-entities-on-azure-waf-2/
Azure Frontdoor is a powerful tool for managing web traffic, but it doesn’t always provide enough protection against malicious incoming requests. In particular, it doesn’t have a built-in feature for blocking IP addresses that are scanning for vulnerabilities or behaving abusively. To address this issue, I created a function app that allows you to block abusive hosts for a period of 24 hours (depending on the data set used).
It’s worth noting that this process does require some technical knowledge and research. But with a little effort, you can create a function app that provides an additional layer of protection against malicious traffic.
Create App Registration
Create an App Registration in Azure AD. This will allow you to create a secret that you can use to authenticate your function app. Make sure to save the tenant ID, application ID, and secret for later use.
Set Access Rights on WAF Policy
Assign the app owner rights on the WAF Policy that you want to update. This will give the function app the necessary permissions to modify the policy.
Create an Azure Function App
Create a new Function App using C# and an HTTP trigger. You can find the code for this function app in the link below. Make sure to note the Function App URI once it’s deployed, as you’ll need it later.
Update the code in the cs file with your specific values. This will include the tenant ID, application ID, secret, and Function App URI that you obtained earlier.
https://github.com/JeroenP87/BlockAbusiveWAFHosts/blob/main/BlockEntitiesWAF.cs
public static string secret = "";
public static string appid = "";
public static string tenantid = "";
public static string azureid = "Azure Subscription ID";
public static string resgrp = "ResourceGroup";
public static string wafpolicyname = "WAFPolicyName";Sentinel
In addition to setting up the function app, it’s important to have a well-configured Azure Sentinel environment that imports all Frontdoor traffic. This will give you visibility into the traffic flowing through your web application and allow you to identify any potential threats.
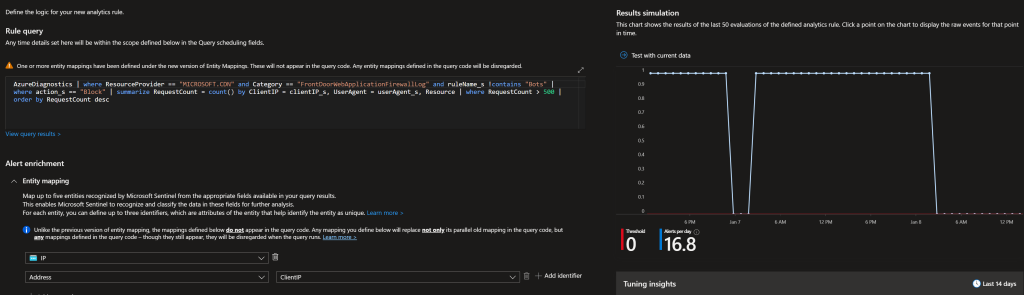
If don’t have any analytic rules yet, you can use the following query. This query will pull data from the past day and block all IPs that hit the 500 blocked requests limit.
AzureDiagnostics
| where ResourceProvider == "MICROSOFT.CDN" and Category == "FrontDoorWebApplicationFirewallLog" and ruleName_s !contains "Bots"
| where action_s == "Block"
| summarize RequestCount = count() by ClientIP = clientIP_s, UserAgent = userAgent_s, Resource
| where RequestCount > 500
| order by RequestCount descIt’s recommended to run at least once every hour to ensure that any malicious IPs are blocked in a timely manner. Make sure to map the entities correctly, those will be posted to the Function App.
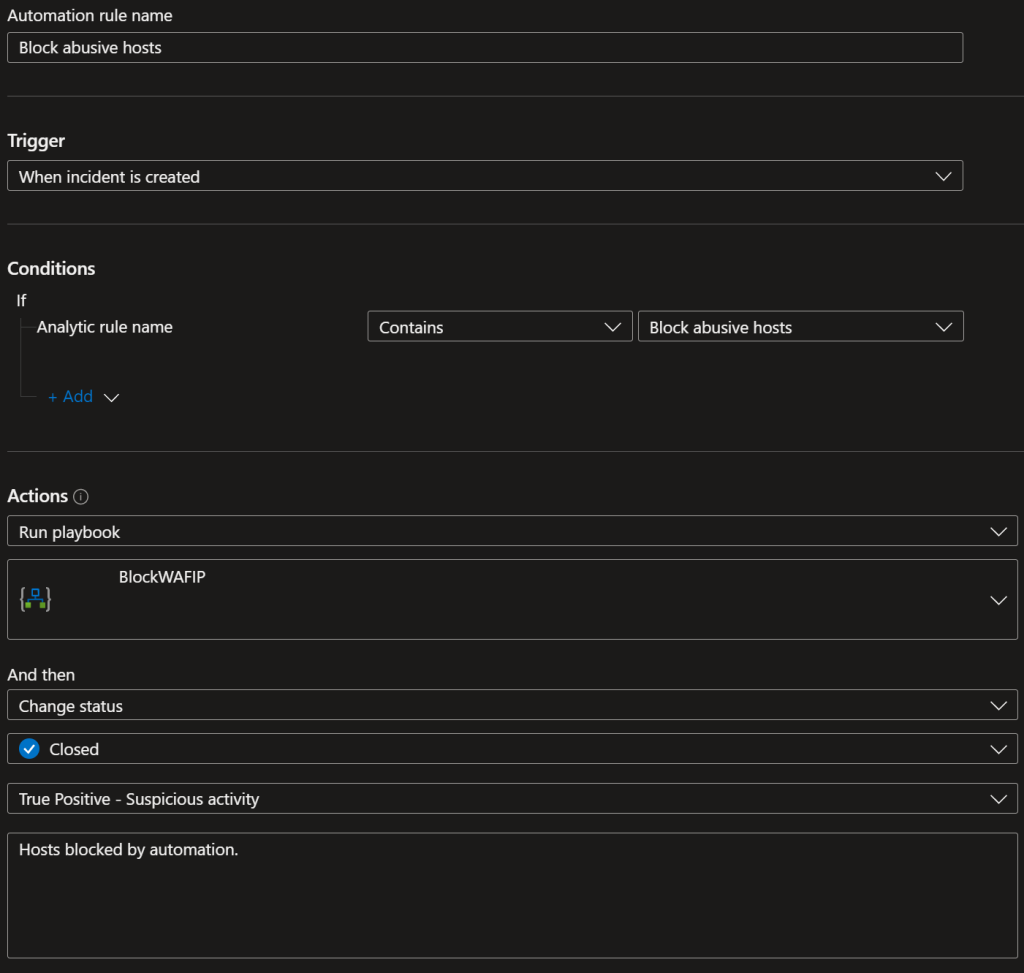
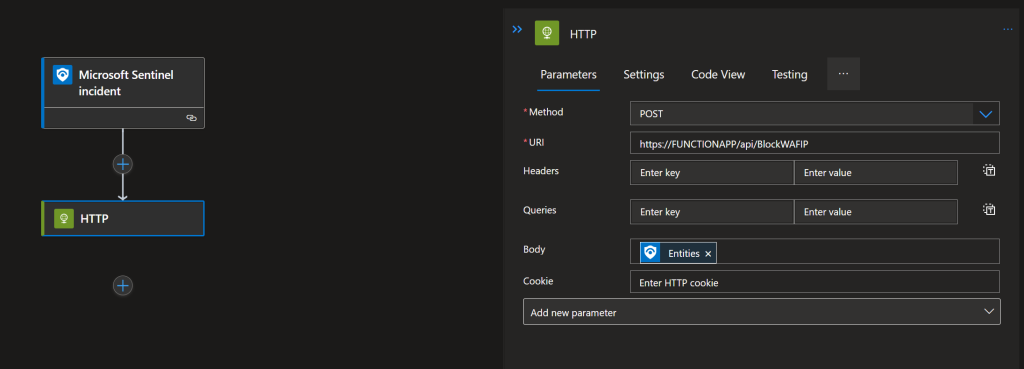
Logic app that sends entities from the Sentinel incident to the function app API.
The setup process for this should be relatively straightforward. Once you have created the analytic rule in Azure Sentinel, you can use the Logic App to trigger the function app API whenever the rule is triggered. This can be done by configuring the Logic App to trigger on new incidents in Sentinel.
You can also configure the Logic app to automatically close the incidents in Sentinel after it sends the entities to the function app API, as the rules are triggered hourly depending on the amount of traffic, this way you can keep track of the incidents and avoid unnecessary noise.
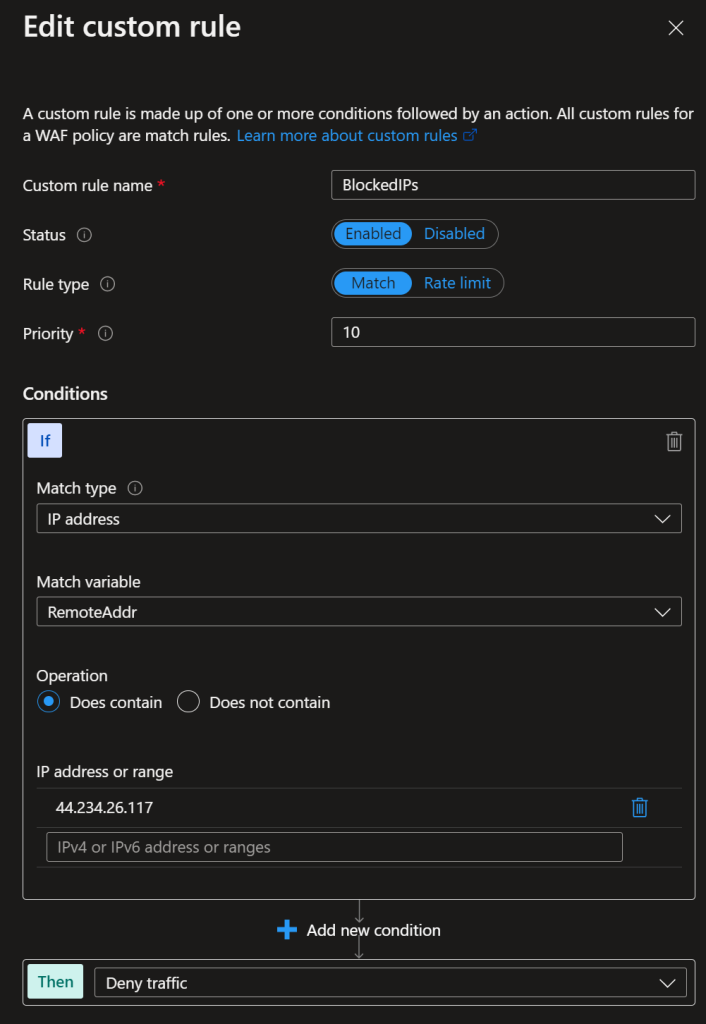
WAF Policy
To complete the setup process, you will need to add a custom rule “BlockedIPs” to the WAF Policy. This rule will be used to block the IP addresses identified by the Azure Sentinel analytic rule. Set it to Match type IP address & Does contain + a bogus IP address.
The function app will receive the IP addresses from the logic app returned by the Azure Sentinel analytic rule. Any values in this rule will be overwritten with values received.
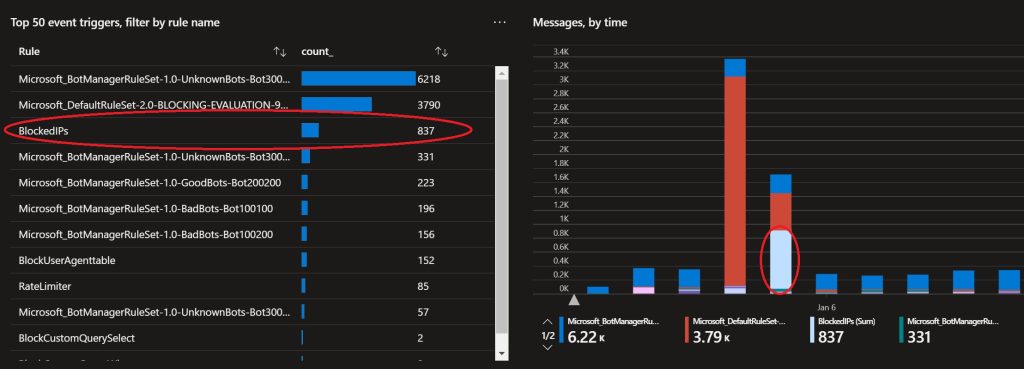
Result
Below a example of requests that are blocked that would not have been blocked by any other rule.
Test with Postman
You can easily test the function app by using a tool such as Postman. To test the function app, you will need to send a POST request to the function app URI with the necessary data in the body.
To: FunctionAppURI/api/BlockWAFIP
[ { "id": "", "type": "Microsoft.SecurityInsights/Entities", "kind": "Ip", "properties": { "address": "SOMEIP", "friendlyName": "SOMEIP" } }, { "id": "", "type": "Microsoft.SecurityInsights/Entities", "kind": "Ip", "properties": { "address": "SOMEIP", "friendlyName": "SOMEIP" } } ]All done!
Keep an eye on the Sentinel Incidents or add an notification to the logic app. This automated process will help ensure that any malicious IPs are blocked quickly and efficiently, improving the overall security of your web applications.

No responses yet